By Mary Grlic
Ransomware has become far more of a threat than ever before for countless companies. As technologies evolve, cyber threats unfortunately become more common. Even newer security methods are sometimes not enough, as hackers could always be one step ahead. You’ve probably seen a lot of ransomware articles in the news, including attacks on healthcare, manufacturing, and other industries. These attacks can happen anywhere at any time, which is precisely what makes it so concerning. Ransomware has evolved significantly since its first appearance over thirty years ago. Let’s look at the evolution of ransomware over time.
What is Ransomware?

Ransomware is any malware that hackers put onto devices, files, and servers to make them unusable. They will use an “encryption key” that is only known to the hacker, essentially locking such files. When the ransomware locks these files, the user can no longer access them. The hackers may hold that data “ransom” and ask for something in return to retrieve that information. Victims might have to pay a “ransom fee” to get their encrypted data back. Ransomware can be spread through many different ways, including phishing scams and other computer viruses. It’s become such a huge threat because devices can now be taken over in just one click.
The Beginning of Ransomware
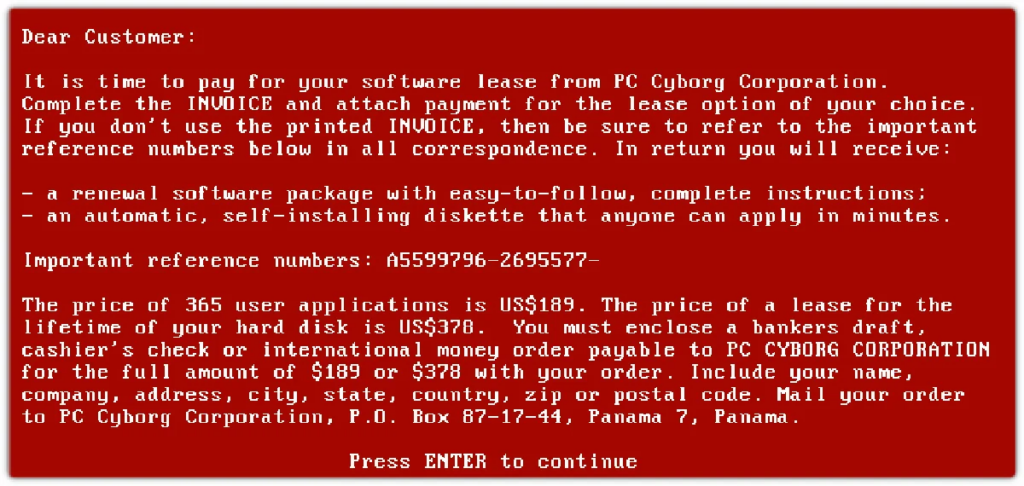
AIDS Trojan/PC Cyborg

In 1989, the first known ransomware attack occurred against the healthcare sector. Joseph Popp, PhD and AIDS researcher, attacked a healthcare group by distributing 20,000 floppy disks to researchers in over 90 different countries. The disk had a malware program that stayed in computers and activated after the device was powered on 90 times. Then, the computer would show a message demanding a ransom fee and a software lease. This became known as the first ransomware attack called the AIDS Trojan or PC Cyborg. Evolution following this ransomware attack was slow but this is where it began.
Ransomware Since Then
The first ransomware attacks were very rudimentary. They took a while to execute and were very simple compared to modern day attacks. Hackers would typically write their own encryption code, which took a considerate amount of time. Nowadays, hackers utilize different tactics and ask for a lot more money. They rely on “off-the-shelf” code, which is significantly easier to program and deploy.
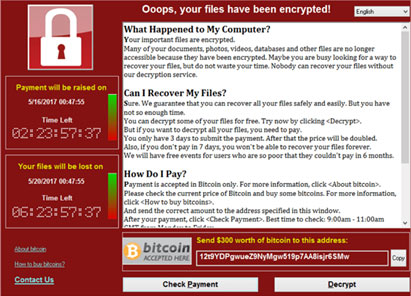
Ransom fees can vary depending on the company or person being targeted, ranging anywhere from hundreds to hundreds of thousands of dollars. In 2016, Hollywood Presbyterian Hospital in Los Angeles had to pay more than $17,000 in bitcoin ransom but believe it or not, that number is on the smaller end. Ransomware attacks could (and have) cost millions of dollars for some bigger name companies. The FBI acknowledges that, the actual historic data available regarding ransomware attacks might be “artificially low.” This includes how many attacks have occurred, and the ransom fees that have been demanded and paid. So why is that? The answer is this case is simple. It’s embarrassing for companies to admit they’ve been targeted or “got,” and many often worry how the news of such an attack would affect future business. With that in mind, it’s evident that ransomware is an even greater threat.
Crypto and Ransomware

Cryptocurrency (digital money) has also became a big player in the ransomware game, mainly because of it’s lack of traceability. With the rise of digital money like Bitcoin, it became a lot easier for hackers to hold data ransom and demand money through these digital currencies. Cryptocurrency makes it easier for hackers to stay anonymous and quickly receive large sums of money, making it a win-win situation for them. A blockchain data analytics company, Chainalysis, reports that in 2020, hackers and “malign actors” received at least $692 million in cryptocurrency due to ransomware attacks. Although law enforcement officials and service providers have the technology to trace cryptocurrency transactions, hackers might be able to cheat the system here. They might use tactics to confuse officials so that they are not caught by using exchanges that “mix” currency to avoid tracing.
Evolution of “Locker” Ransomware
In 2007, cyber attackers performed the first example of “locker” ransomware, in which they targeted victims by locking their machines and preventing them from using basic computer functions. The device then prompted the users to call a “premium-rate phone number” or send an SMS message in order to pay the necessary ransom demands. Since then, the idea of “locking” or “encrypting” computers, devices, and data has become the key to ransomware attacks.
In 2013, cybersecurity professionals discovered a new ransomware called “CryptoLocker,” which self-installed onto Windows devices and affected their “Documents and Settings” folder. The ransomware then uploaded a small file to generate what is known as an encryption key to encrypt documents, files, images, and more data on the user’s device. The device would then display that the user had 72 hours to pay a ransom fee. Hackers use locker ransomware to encrypt files and data on a victim’s device and demand a ransom fee to unlock these files.
Evolution and Changes in Ransomware Today
Even with the evolution of ransomware over the past thirty years, it’s still something that continues to change. After seeing multiple headlines speaking of ransomware attacks, it’s clear that it’s not something that’s going away anytime soon. Within the past year, for example, Maui ransomware hit the healthcare industry, which encrypted files and servers in hospitals, making PHI (personal health information) inaccessible. Sonicwall’s 2022 mid-year report explains some of the trends and changes in ransomware.
Data Exfiltration as Ransomware

A new custom data exfiltration tool seems to be posing an even greater threat in the world of ransomware. Known as Infostealer.Exbyte, the data exfiltration tool takes victim information to steal and expedite theft. BlackByte is a ransomware-as-a-service operation run by a cyber-crime group known as Hecamede. They utilize Exbyte to check for any “sandboxes” in the environment that they are trying to affect, as well as to monitor for antivirus tools. A “sandbox” is a system for malware protection, so clearly if a device has a sandbox, the attacker will be unsuccessful with actually executing their goal. The tool then searches through the device or profile for documents that they upload to a cloud-based account. Exbyte is just one example of a data exfiltration tool. Researchers from Symantec note that it’s similar to tools like Exmatter, Ryuk Stealer, and Stealbit.
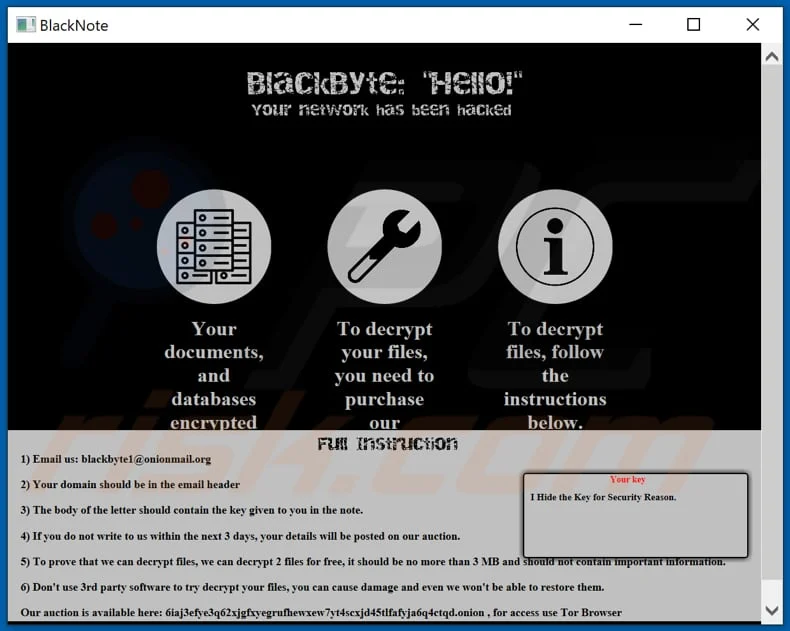
How it differs from encryption
The key difference between data exfiltration tools and typical ransomware is the idea of encryption. As mentioned earlier, attackers usually use encryption in ransomware attacks, so that they can “lock” files and documents with an encryption key. Exfiltration, however, suggests a news threat that can change the whole world of data theft as we know it. Having secure, fast ransomware to encrypt files is simply becoming more redundant, slow, and costly, as researchers from Cyderes said. Some ransomware actors actually lost out on any financial or monetary gain through their attack simply because of faulty ransomware.
Hackers are often trying to discover the sneakiest, quickest, and cheapest way to accomplish their goals, and with new tools like data exfiltration, they may start leaning towards this method. With the evolution of data exfiltration, ransomware attackers can actually steal data instead of encrypting it, meaning they’ll get the job done a lot more quickly. Technologies like these make ransomware an even greater threat. This leads us to question: what is the future of ransomware?
The Future of Ransomware: What’s Coming Next?
Cybersecurity experts can agree on one thing: ransomware is not going away. In fact, the number of attacks will only increase in years to follow. Attackers keen on compromising systems and demanding ransoms in exchange for relinquishing the data, are becoming more sophisticated with new and advanced techniques like extortion and data exfiltration. These methods make ransomware far more dangerous.

Ransomware has the ability to shut down small businesses, impact government functions (even shutting down county government, as in Suffolk County, NY), take down critical infrastructure (like healthcare), impact the production of news/papers (as with The Guardian‘s attack) and even harm national security. These threats will become even more critical in the future. Luckily with a proper plan in place, businesses and individuals can protect themselves from a ransomware attack. Many high-level organizations and cyber professionals understand the dangerous risks that such an attack can pose. Taking action and the proper steps to prevent ransomware is the best way to keep your company safe. Some examples include proper cybersecurity awareness training and having a good antivirus on business-grade devices. Read our article about ransomware to learn more.





0 Comments