The Internet of Things – IoT – has changed the way that we connect to the rest of the online world. These devices can communicate with the internet to simplify tasks, like changing the temperature on your thermostat or playing a certain song. Many homes and businesses have begun to, or are looking to deploy IoT devices, without realizing the potential security and privacy risks that come with them. With the increase in IoT malware, these devices are just one more thing that manager service providers suggest you look out for. IoT describes physical devices (things) that have certain softwares and sensors so that they can communicate with other devices over the internet. Common examples of IoT devices include Amazon Echo and Amazon Ring, as well as other Amazon Alexa powered or compatible devices, as well as smart TVs, and even wearable smart watches like the FitBit or Apple Watch.
Understanding the Internet of Things (IoT)
Items that we use on a daily basis are now being equipped with IoT technologies, making for seamless communication and almost robotic-like interactions and activities. Vacuum cleaners, thermostats, cars, and even baby monitors can all be connected to the internet using embedded devices. The number and capabilities of IoT devices are only increasing. Many residences and businesses have been investing in these technologies in recent years due to their convenience and ease of use, however, as with most things, this convenience might come at a cost – and a big one at that.
Sure, we love devices that make our lives easier. Why vacuum your house when Roomba can do it for you? If you hate the song you’re listening to while friends are over, simply tell Alexa or Google to switch the tune. Now it’s easy to keep track of all of your steps and calories by wearing a smartwatch. Know exactly when the postman is at your front door with your Ring doorbell camera. You might even be able to turn on the heat or AC in your car just with the tap of a button on your cell phone. Seems like a no-brainer to start buying some IoT devices for your home or office, right? Wrong!
An Unsettling Threat: IoT Malware
The number of IoT malware threats seemed to be on the decline after the massive 218% jump in 2019. There was a 66% decline in 2020 and an additional 6% decline in 2021, creating some hope for the downward trend of IoT malware. However, in 2022, IoT malware nearly doubled, with an increase of 81% over 2021 according to SonicWall’s 2023 Cyber Threat Report. The massive spike compared to previous years is quite unsettling, and shows us that even with seemingly downward trends, any type of cyber attack can always make a return.
With more smart devices scattered across homes and offices, it makes sense that the amount of IoT malware attacks would increase. Cyber attackers see it as a target with the number of devices on the rise and the lack of proper IoT security measures that many of them might have. IoT malware exploits vulnerabilities, weak credentials, and other means. According to SonicWall, IoT devices are not very powerful on their own, so attackers will deploy massive amounts of malware to create “botnets” on the infected devices. A botnet can be controlled by either a group or an individual hacker, and botnets can operate the device behind the device owner’s back. Now the IoT devices are infected with malicious software that is controlled by an external, unauthorized user. They will use either a command-and-control server or peer-to-peer network, and once connected, they will perform malicious activities. With IoT malware, victims might suffer a Distributed Denial of Service (DDoS) attack, cryptojacking malware, brute force attacks, ransomware, data theft, spam, or more.
Internet of Things (IoT) Security Concerns
The internet of things comes with many challenges that might pose a huge vulnerability to your system. When IoT devices exist on the same network as every other device, this creates a huge security concern for consumers. IoT devices oftentimes have unpatched vulnerabilities and open-source code vulnerabilities that make them an easy target for cyber attackers. The firmware behind IoT is open-source, making these devices especially vulnerable to bugs and other threats. These devices have vulnerable API – application programming interfaces – which is the way that computers interact with each other. APIs are often the opening at which attacks are launched, including DDoS, man in the middle (MITM), SQL injections, and more. When vulnerable IoT devices exist on the same network as business servers, personal computers, and more, any device on that network is at an increased risk. If the IoT device is to get hacked, the attacker now has access to anything and everything on that network. This is why IoT malware is such a huge concern – it does not only affect the devices, but IoT malware can also have a massive impact on the entire network.
Software and Firmware Vulnerabilities
Many IoT devices are not even properly tested by the companies that create them, exposing the consumers that then purchase these devices to a plethora of risks. There is oftentimes a lack of computational capacity for efficient built-in security. A major risk is simply that these devices do not have the right capabilities to actually stay protected against cyber crime. They lack updates, proper safety, regular patches and vulnerability updates, and more, leaving them at a huge disadvantage.
Emerging Threats
Some newer IoT security threats include the complexity of device management, increase in remote work, and use of 5G/data. Many homes across the United States are starting to incorporate more and more IoT devices on their network. This makes it more challenging to properly oversee and manage all of these devices at once. One device gets misconfigured, and this could drastically harm your home network security. Working from home and hybrid work also seems to be a concern when it comes to IoT. Households that already have IoT might experience some trouble when creating a work from home network setup. The transition to 5G poses some questions, and will result in various changes for the many different technologies that operate on it, especially IoT devices. Adjusting to this technological shift will result in some unforeseen challenges.
Internet of Things (IoT) Privacy Concerns
You might be familiar with the concept that your devices (such as your smartphone) can “listen” to what you’re saying. Think about it: for things like Alexa, Google Assistant, and Siri, your devices always have to be listening for that “Hey Alexa” or “Hey Google.” This is such a convenient feature that allows users to fulfill a wide array of tasks, like playing a certain song or turning on the lights, simply with the use of voice commands. However, it leads us to question just how private these devices are, considering that they are literally listening for certain words at all times. This is just one tangible example when it comes to IoT privacy and security concerns but there are more that might be questionable for users, like the amount of digital data these devices host and an unwanted public profile.
Keep in mind that companies like Google, Amazon, Apple, and others do have privacy policies to protect users to some degree but to what extent? The fact that these IoT devices are “live and listening,” poses a huge concern for businesses and individuals when it comes to privacy and confidentiality. Some other IoT devices that might take advantage of personal data include security cameras, which have already posed substantial privacy concerns in recent years.
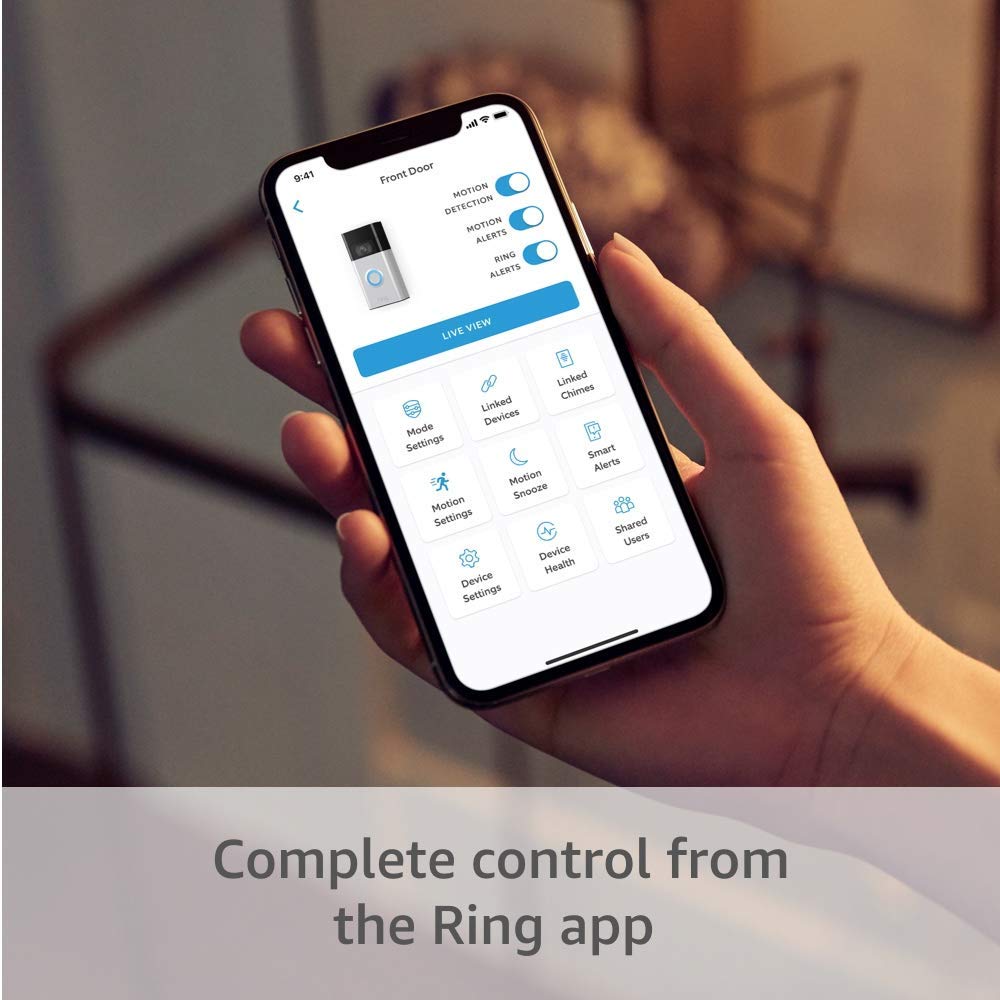
Amazon Ring Might Protect Your Front Door but Not Your Data
Amazon Ring video doorbells, for example, have an unfortunate reputation in terms of IoT security and privacy. This device seems like a great option to keep your home safe. “Smart” doorbells like Ring have features like video-capturing and motion detection. This way, users can always know who is at the door, whether it’s the mailman, a friend, or even a package thief! However, while these doorbells seem like a perfect solution to keep your home safe, there are some huge privacy concerns with the way they function.
Amazon’s Ring has a bad history of data leaks and third party tracking. In 2020, the company introduced two-factor authentication for Ring devices, which was a huge step forward in the world of cybersecurity. However, this didn’t eradicate all of the privacy concerns for Amazon Ring. In fact, in a July 2022 press release, Massachusetts Senator Edward J. Markey revealed that Amazon admitted to sending Ring footage to the police without user consent or court order 11 times that year. Markey’s ongoing investigation also revealed that Ring failed to disclose the distance at which the devices can capture audio recordings, refused to make end-to-end encryption the default storage method, and did not eliminate the default setting of recording audio, among other things.
Amazon Gets Hit With One Lawsuit After Another
Despite Ring’s terrible history, Amazon still doesn’t seem to learn and has continued to fail to prioritize data security. The Federal Trade Commission (FTC) claims that the company has misused data through two of Amazon’s IoT devices, Alexa and Ring. Amazon Alexa is a virtual technology voice assistant. People can tell Alexa to play music, turn on the lights, search something up on Google, and so much more. However, behind all these tasks that Alexa does seem to simplify, the device actually listens to what users are saying. This data has been misused by Amazon, despite both their privacy policies and various claims not to do so. Amazon allegedly recorded and stored children’s conversations with Alexa in order to illegally “improve its algorithm.” The employees responsible for this also refused to delete these recordings, undermining the parents’ requests and attempting to keep them forever. This goes against the Children’s Online Privacy Protection Act (COPPA) which “imposes certain requirements on operators of websites or online services directed to children under 13 years of age, and on operators of other websites or online services that have actual knowledge that they are collecting personal information online from a child under 13 years of age. Amazon is now facing a $25M civil penalty, as per the FTC and DOJ (Department of Justice) for violating children’s privacy.
In addition to the Alexa breach, an Amazon employee also used Ring cameras to spy on users. This individual specifically searched for cameras located in bathrooms and bedrooms to watch the footage of more than 80 women and some Ring employees without their consent. This filing is a part of a $5.8M lawsuit against Ring and Amazon for their failure to “restrict employees,” and contractors’ access to its customers’ videos.” This appears to be a persistent issue for Amazon that, for one reason or another, still hasn’t been fixed, despite multiple occurrences. To make matters even scarier, it’s unclear just how many employees and users could have viewed the footage. Once it was in the hands of one, it may have been leaked to others. In fact, the single employee spent months in 2017 watching thousands of recordings against users’ will.
With just these two instances alone, Amazon is forced to pay about $30M dollars in charges. It’s a bit spooky how easily such a reputable company could possibly get away with such huge privacy breaches. It makes you wonder how much all of that data must be worth; it seems like just having it is worth far more than actually securing it.
Why Does This All Matter?
While not entirely unusual (given their history), Amazon continues to remain incredibly secretive about what’s being done with consumer data, and clearly, plans to continue to exploit user privacy. Ring is just one example of an IoT device that has posed countless privacy concerns for users. So long as big name companies like Amazon are at the forefront of such lawsuits and privacy breaches, we’ll continue to hear about them as they’re uncovered and huge fines will be the price they pay for the lack of security. It takes one poorly trained, untrustworthy employee to create such a mess for a product and its end users. Places that once seemed safe – like our kitchen or bedroom – are now at risk. The unfortunate reality is that these IoT devices can watch or listen to everything. It’s clear that just about anyone, whether it’s an employee or total stranger, could access these recordings without your knowledge, making for quite a frightening reality.
Smart devices and IoT collect and track a lot of data. Think about something like a smart watch, which tracks your daily steps, heart rate, movement, hours of sleep, calories burned, etc. This information is then stored in an app or on a server elsewhere. It’s crazy to think that devices like these are literally tracking and analyzing human consumption, down to a person’s every move. And unfortunately, even if someone decides not to use any IoT in their home or office, they can still be present in public. So many smart devices, like security cameras, are analyzing human behavior in public areas, leading people to question the extent that their privacy is being protected. At the end of the day, there could be someone behind the screen exploiting you – all because of the IoT device in your home. It’s a scary and unfortunate reality, simply due to the inadequate security and privacy measures these companies have put in place.
Keeping Internet of Things (IoT) Devices Safe & Secure
After learning about the various IoT security and privacy concerns, you might be wondering how you can protect yourself from these issues. IoT devices are convenient and surely something that many consumers already have access to in their residences or businesses. In today’s day and age, it can even be difficult to live without these devices, especially when we’re so conditioned to having them right by our side, or even on our person.
Many companies are ready to deploy Internet of Things (IoT) devices in the office or elsewhere to help business. Some have already started using IoT, but do they have the right measures in place to maximize security and protect privacy? AT&T Cybersecurity Insights Report says that only 10% of surveyed enterprises feel prepared to protect IoT devices in the event of cyber attacks and such. Clearly, this leaves businesses with a huge concern, and forces us to pose the question: how can businesses keep their network safe and secure when IoT devices are a part of it?
Inform Your IT Department of All IoT Devices
This suggestion especially goes for businesses and individuals who work from home. Many employees and contractors may implement these devices into their homes and routines without thinking twice, and without considering mentioning it to their IT department. If your managed service provider is unaware that these devices exist, they won’t have an accurate assessment of everything that should be secured, as well as monitored. Just like any other devices on your network, including servers and computers, your IT department must have knowledge of any IoT devices to be able to safeguard your network from any threats.
Have Internet of Things (IoT) Devices on a Separate Network
As mentioned earlier, Internet of Things (IoT) devices face several vulnerabilities that make them an easy target for hackers. Once cyber attackers gain access to your IoT device, they can infiltrate the entire network and any device on that network. This means that data on servers or personal computers is at immense risk. Segregate IoT devices from other devices by putting them on separate networks, so that these devices cannot communicate with one another. This means different ports to separate IoT devices from the others, that way the IoT device can only communicate with itself and the internet. At Computero, we follow this procedure with any of our business customers that utilize IoT devices. We understand that sometimes having IoT is a necessity or perhaps just, such an irresistible convenience. Despite their possible security flaws, we’ll be sure to take all of the possible precautions to protect your entire network despite them.
Understand the Risks
As with any new device or implementation of software, it’s important that employees and businesses understand the risks involved. Use Internet of Things devices with caution, and always be aware of any privacy or security concerns surrounding them. Research the device; even if it seems reputable, there still could be previous concerns regarding the company or even a history of data breaches. Take Amazon Ring as an example: even though it’s a widely used device, there are still huge privacy breaches that have occurred countless times. These IoT security incidents shouldn’t be overlooked.