How Do We Know Security Keys Are Worthwhile?
The value of security keys has been thoroughly examined by one of the most tech-obsessed, and industry-dominating, tech companies: Google. What they learned was this: Security keys are the #1 absolute, best form of two-factor authentication (2FA). It’s better than an on-device prompt, a secondary email address, an SMS code, a phone number, and last sign-in location. How do we know this? Don’t worry, we’ll get into that but first, we have a request: a willingness to shift your perspective.
We’re aware that there are a variety of methods when it comes to 2FA but we’d like to urge you to not look at 2FA like they’re flavors at an ice cream parlor. 2FA should be about security first and foremost, not so much about “what feels right.” 2FA is not your favorite pair of jeans, your cheat meal or your daily driver; it doesn’t require that much thought or emotion. What you should know is that a poorly chosen form of 2FA (in other words, a lesser version, based on the findings) could cost you everything.


We know that 2FA is, for lack of a better expression, a pain in the butt, and we know that New Yorkers, such as ourselves even, might describe it as, “mad annoying” (and BTW, we don’t disagree) BUT the slight irritation remains a worthwhile sacrifice when we consider how enmeshed our personal and business lives have become with technology. If you’re still wondering at this point, “What’s wrong with using my phone for two-step verification,” this is why your phone sucks when compared to security keys.
Google Studies
Google highlighted the benefits of Security Keys in a two-year deployment study that dates back to 2016, titled “Security Keys: Practical Cryptographic Second Factors for the Modern Web.” Within the study, they point out the flaws of OTPs (one-time passwords) as a form of 2FA (two-factor authentication) and use the Yubikey Security Key by Yubico as the remedy. What they discovered within those two years was compelling and because of it, they managed to eliminate phishing attacks against all Google employees completely (meaning: a 100% success rate). They found that while OTPs had an average failure rate of 3%, that U2F (Universal 2nd Factor), the technology that security keys utilize, had a 0% failure rate. In fact, if you review the literature, you’ll see that security keys are the ONLY form of 2FA that are fully resistant to phishing and THAT is key, no pun intended.


If you’re reading this in 2023, then we should all take a moment to realize that 2016 was seven years ago. We understand that not everyone always stays up to date on the latest technology (“so much to do, so little time”) but why physical security keys aren’t yet a standard, after all that time, is a bit of a shock to us. Let’s also note that Google’s claims weren’t hypothesized, they were sufficiently documented over the course of two years, and not even just documented but published for the good of all.
“For the deployment, we found the increased user productivity …[was] worth the increased hardware cost.” (Google Study 2016, pg 15)
“Security keys require no batteries and usually have a dedicated tamper-proof secure element.” — (Google Study 2016, pg 2)
Google’s 2019 Study | A Collaboration with NYU & UC San Diego
To further investigate just how effective basic account hygiene is when it comes to preventing hacking, Google conducted another study in 2019: “Evaluating Login Challenges as a Defense Against Account Takeover.” This time around, they collaborated with NYU and UC San Diego. The study was a year long and it focused on both wide-scale and targeted attacks. We’re happy to provide the bullet points of their findings as well but this graphic from Google (see below) beautifully sums up their findings. While Google doesn’t mention the word, “security key,” all that much in the article blog publication of their findings (only once, actually), it’s mentioned 18 times in the published version of the study and the biggest takeaway is this: “Zero users, that exclusively use security keys, fell victim to targeted phishing during our investigation.”
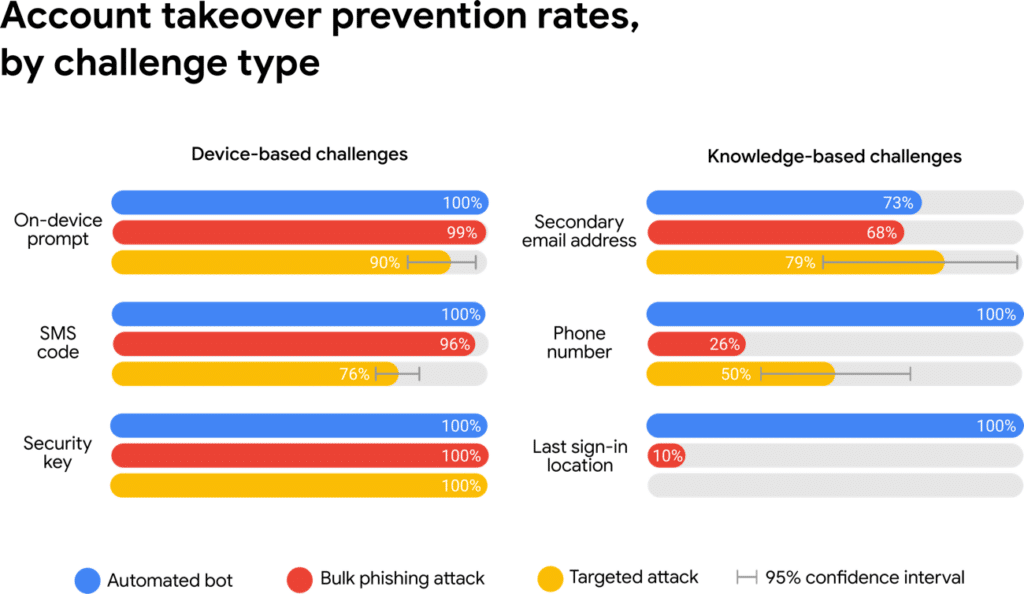
Other account security findings from Google’s 2019 Study:
- Simply adding a recovery phone number to your Google Account can:
- block up to 100% of automated bots
- 99% of bulk phishing attacks
- 66% of targeted attacks that occurred during our investigation
- We found that an SMS code sent to a recovery phone number helped:
- block 100% of automated bots
- 96% of bulk phishing attacks
- 76% of targeted attacks
- On-device prompts, a more secure replacement for SMS, helped prevent:
- 100% of automated bots
- 99% of bulk phishing attacks
- 90% of targeted attacks
Some other worthwhile metrics include Google’s comparison chart that breaks down usability and security concerns. This was taken directly from the, “Evaluating Login Challenges as a Defense Against Account Takeover” study.
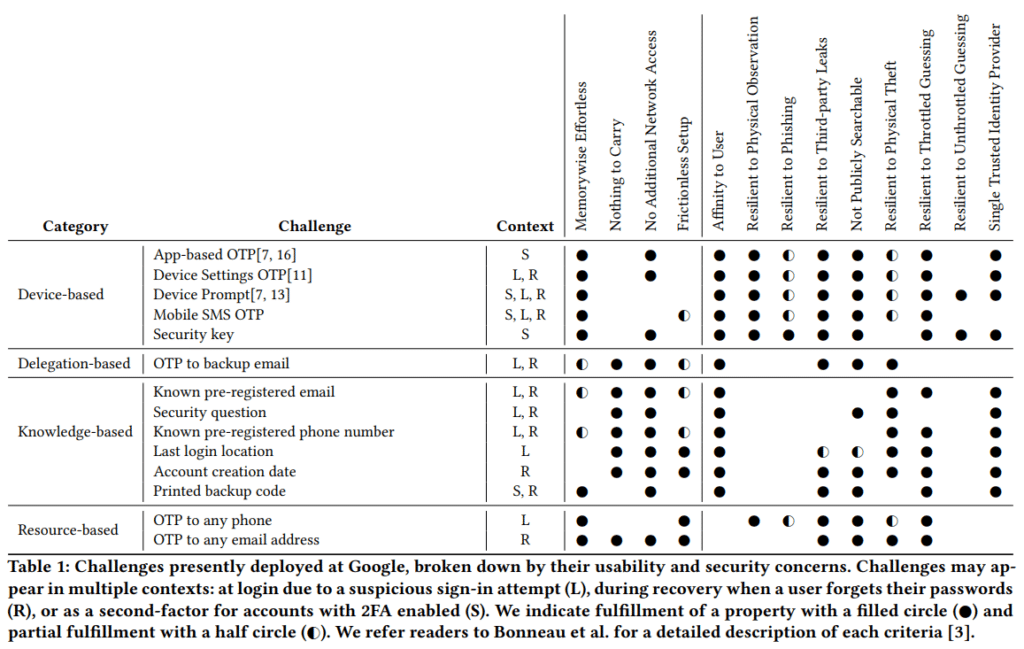
2FA Challenges
Each 2FA challenge lacks some of the criterias listed above (see the vertical lines of text above in Table 1), and the 2FA challenges that lacked the least, all lacked in a total of 3 criterias. There’s 4 of them. They are: App-based OTP, Device Settings OTP, Device Prompt, and Security Key. A filled circle represents “fulfillment of a property,” and a half circle represents, “partial fulfillment.” Here’s a table of a clearer breakdown, with our take on what “partial fulfillment” means; it means the glass is half empty, not half full.
| CRITERIA | App-based OTP (Challenge) | Device Settings (Challenge) | Device Prompt (Challenge) | Security Key (Challenge) |
| Memorywise Effortless | ✔️ | ✔️ | ✔️ | ✔️ |
| Nothing to Carry | ❌ | ❌ | ❌ | ❌ |
| No Additional Network Access | ✔️ | ✔️ | ❌ | ✔️ |
| Frictionless Setup | ❌ | ❌ | ❌ | ❌ |
| Affinity to User | ✔️ | ✔️ | ✔️ | ✔️ |
| Resilient to Physical Observation | ✔️ | ✔️ | ✔️ | ✔️ |
| Resilient to Phishing | ❌partially | ❌partially | ❌partially | ✔️ |
| Resilient to Third-party Leaks | ✔️ | ✔️ | ✔️ | ✔️ |
| Not Publicly Searchable | ✔️ | ✔️ | ✔️ | ✔️ |
| Resilient to Physical Theft | ❌partially | ❌partially | ❌partially | ❌ |
| Resilient to Throttled Guessing | ✔️ | ✔️ | ✔️ | ✔️ |
| Resilient to Unthrottled Guessing | ❌ | ❌ | ✔️ | ✔️ |
| Single Trusted Identity Provider | ✔️ | ✔️ | ✔️ | ✔️ |
If you find this interesting and want to educate yourself further, here are some other studies, including the ones we referenced already:
| YEAR | COLLABORATORS | RESEARCH |
| 2019 | GoogleUC San Diego | Hack for Hire: Exploring the Emerging Market for Account Hijacking |
| 2019 | GoogleNYU | Evaluating Login Challenges as a Defense Against Account Takeover |
| 2017 | GoogleUC San Diego | Data breaches, phishing, or malware? Understanding the risks of stolen credentials |
| 2016 | GoogleYubico | Security Keys: Practical Cryptographic Second Factors for the Modern Web |
Why Physical Security Keys Are the Best Form of 2FA (& How They Work)
Security keys like Yubico offer several advantages over other 2FA (two-factor authentication) methods, which contribute to their enhanced security:
1. Phishing resistance
Security keys are immune to phishing attacks, where attackers trick users into entering their credentials on a fake website. Security keys use a cryptographic protocol called FIDO2/WebAuthn, which verifies the authenticity of the website, ensuring that login credentials are only shared with legitimate sources. This protection significantly reduces the risk of falling victim to phishing attempts.
2. Hardware-based security
Unlike other 2FA methods such as SMS-based codes or authentication apps, security keys are physical devices. They store cryptographic keys securely within the hardware, making them less susceptible to malware, viruses, or other software-based attacks. The private keys never leave the device, adding an extra layer of protection. Additionally, Yubikey comes attached to a USB that can’t be identified; it’ll be impossible to know which machine or device it goes with, although the keys attached to it could be a giveaway if colleagues are familiar with yours.
3. Strong cryptographic algorithms
Security keys utilize strong encryption algorithms and protocols to generate and store cryptographic keys. These algorithms, such as ECC (Elliptic Curve Cryptography) and RSA (Rivest-Shamir-Adleman), provide robust security for authentication and data encryption.
4. Offline functionality
Security keys function offline, meaning they do not rely on an internet connection to generate authentication codes. This attribute makes them resistant to attacks that target online communication channels, such as man-in-the-middle attacks or interception of authentication codes.
5. Easy to use and universal support
Security keys, like Yubico, typically follow open standards such as FIDO2 and U2F (Universal 2nd Factor), making them compatible with a wide range of devices, platforms, and services. They can also be used with computers, smartphones, and online services that support these standards, offering a seamless and user-friendly experience.
It’s important to note that while security keys provide significant security advantages, no authentication method is entirely foolproof. However, by combining a security key with other security measures, such as strong passwords and regular software updates, users can significantly enhance their overall security posture.
“YubiKeys don’t ask you to manually type a code, so they’re free to use much longer codes. That’s more secure.” —Zapier
“The FIDO Alliance was founded by PayPal, Lenovo, Nok Nok Labs, Validity Sensors, Infineon, and Agnitio, and work on a passwordless authentication protocol began.” —FIDO
“The Security Key protocol has been standardized within the FIDO Alliance organization as the Universal Second Factor (U2F) open standard.” —Google
Cons of Older Forms of 2FA
Telephone calls, mobile prompts, and text messages as forms of 2-step authentication (also known as SMS-based authentication) have been widely used in the past but are now considered less secure compared to newer methods like security keys. Here are some reasons why telephone calls, mobile prompts and text messages are so 2020 when it comes to security:
1. Phishing and SIM swapping
SMS-based authentication is vulnerable to phishing attacks, where attackers trick users into providing their login credentials. Hackers can also perform SIM swapping by impersonating the user and convincing the mobile service provider to transfer the phone number to a device they control. This allows them to intercept the authentication messages, compromising security.
2. SMS interception
SMS messages can be intercepted or redirected through various techniques, including SS7 (Signaling System 7) vulnerabilities. Attackers can then exploit these weaknesses to gain unauthorized access to the user’s SMS messages, bypassing the intended security measures.
3. Device vulnerability
Mobile devices can be also susceptible to malware or other security vulnerabilities and threats. If a device is compromised, hackers may be able to gain access to both the user’s login credentials and the authentication messages, defeating the purpose of 2-step authentication.
4. Lack of offline functionality
SMS-based authentication relies on an active network connection to receive text messages. Consequently, in situations where there is no cellular coverage (like a “dead zone”), users may be unable to receive authentication codes. This is a common problem; users will not have coverage 24/7. This hinders their ability to log in to their accounts, which can be a major issue if you need to log into an account in a quick pinch.
5. Limited scalability and convenience
SMS-based authentication requires users to have a valid phone number and may not be suitable for individuals who do not have access to a mobile device or prefer not to share their phone numbers with service providers. Additionally, the process of waiting for and entering a code from an SMS message can be time-consuming (possibly even annoying) and less convenient compared to other methods that will verify your identity.
Due to these security concerns, industry experts and organizations are starting to recommend more secure alternatives more and more. These better alternatives include hardware security keys, authenticator apps, or biometric-based authentication methods. These newer methods offer stronger protection against phishing attacks, interception, and device vulnerabilities, making them more robust and reliable for 2-step authentication.


Pros of Older Forms of 2FA
Here are a few main reasons why telephone calls, mobile prompts, text messages, and code generators are still relevant and widely used for 2-step authentication:
1. Widespread compatibility
Telephone calls, mobile prompts, and text messages are compatible with almost all types of mobile devices and landlines. They do not require additional software installations or specific device capabilities, making them accessible to a broad user base.
2. Ease of use
These methods are relatively simple and straightforward to implement. More often than not, users are familiar with receiving calls or text messages, and the process of entering a code from the message is intuitive. This simplicity enhances user adoption and reduces the learning curve.
3. Availability
SMS-based authentication is available even in areas with limited internet connectivity. Since text messages rely on cellular networks, they can reach devices in remote or low-bandwidth locations where internet access may be unreliable.
4. Non-reliance on hardware tokens
Code generators, also known as authenticator apps, offer a convenient and cost-effective alternative to hardware security keys. They generate time-based or event-based codes directly on the user’s mobile device, eliminating the need for a separate physical token. Many popular authenticator apps, such as Google Authenticator or Microsoft Authenticator, provide an additional layer of security.
5. Familiarity and trust
Despite their limitations, telephone calls and text messages are widely recognized by users as common communication channels. Thus, this familiarity instills a sense of trust and reliability, as users are accustomed to receiving important information through these methods. At the end of the day, it is something we are used to and often use. It’s familiar and easy, making it seem like the perfect solution.
While telephone calls, mobile prompts, text messages, and code generators continue to be widely used, it’s worth noting that newer verification methods such as security keys and biometric-based solutions offer additional layers of security and protection against certain types of attacks. Both new and old methods have their pros and some cons. However, in such a quickly evolving tech world, staying up to date with newer pieces of tech will always be a great option. In this case, security and protection are number one concerns, something you will certainly get with newer authentication methods.
What are the Best Methods for 2FA?
The best method for 2FA depends on various factors, including security, convenience, and user preferences. Here are some commonly recommended methods:
1. Hardware Security Keys
As we spoke about, security keys are a top tier option. Hardware security keys, such as Yubico or Google Titan, offer strong security. They use public-key cryptography to authenticate users and are resistant to phishing attacks. Security keys are portable, easy to use, and provide an offline form of authentication. When users have their security key on them, it is an easy and safe way to log in. They are particularly beneficial for high-security scenarios and are recommended when available.
2. Authenticator Apps
Authenticator apps, like Google Authenticator, Authy, or Microsoft Authenticator, generate time-based or event-based codes on a user’s mobile device. They are convenient and offer better security than SMS-based methods. Authenticator apps can work offline and are not susceptible to SIM swapping attacks or interception of SMS messages. They are widely supported and suitable for most 2FA scenarios.
3. Biometric Authentication
Biometric methods, such as fingerprint or facial recognition, provide a convenient and secure way to verify users. Mobile devices and some laptops have built-in biometric sensors that can be used for 2FA. Biometrics add an extra layer of security as they rely on unique physiological characteristics. However, they may not be universally available across all devices and platforms.
4. SMS or Voice-based Authentication
While SMS or voice calls are not as secure as other methods due to vulnerabilities like SIM swapping and interception, they still provide an additional layer of security compared to using only a password. They are widely supported and can be used when more secure options are not available or feasible.
The best method for 2FA ultimately depends on the specific use case, risk assessment, and user preferences. It is often recommended to use multiple authentication factors (MFA) to provide a higher level of security and redundancy in case one method becomes unavailable or compromised.


Physical Theft Isn’t a Sufficient Defense
Some Thoughts For Those Who Oppose the Notion That Security Keys Are Better
Skeptics like to use the example of physical theft to suggest that security keys aren’t “that secure,” but that doesn’t strip them of all of their value. Cell phones, as an authentication method, are just as worthless when stolen. And what’s more likely? That someone will steal your phone or your keys? If anything is stolen, it’s evident that it can no longer be used for 2FA. That much is clear. Perhaps those that don’t use computers or technology often may require such an explanation but not the mostly-tech-savvy.
It’s not very likely…
Additionally, there are certainly far fewer people who are willing to physically rob you, compared to those willing to compromise you virtually and covertly. We can compare this to keyboard warriors, people who regularly state their opinions, stir up debate and sometimes verbally attack and criticize others on the internet. When given the chance to do the same in IRL (in real life), they’re far less likely to do so. Why is that the case? Because to speak up often means to stand out and standing out goes against our instinct to survive (that’s why it’s so commendable when it is for a good cause and when it is IRL. In the virtual world and on the interwebs, the lines of reality are blurred, as a result of something that’s known as: the online disinhibition effect. There’s a variety of psychological factors that contribute to this type of behavior, including:
- Anonymity
- resulting in a sense of empowerment
- Social identity
- herd mentality, a communal reinforcement of behavior, manners are sacrificed for a “bigger cause”
- Confirmation bias
- a tendency to look for information and perspectives that confirm their own
- Frustration and stress
- expressing frustrations can be cathartic
- A perceived lack of consequences and accountability
- increased aggression and combative behavior can be witnessed when an authoritative presence is (or appears to be) lacking
Physical theft is much less likely than the wild array of cybersecurity threats, as a result of the disinhibition effect. We’re certainly not saying that theft doesn’t happen and that you shouldn’t be cognizant of your surroundings at all times. What we are saying is this: don’t discount the best form of 2FA because it’s not “virtual.” Yes, it’s physical, it has mass but guess what? So do you.
The Cost of a Data Breach, as per IBM & the FBI
IBM released a 2022 Data Breach Report to further educate people about the real implications of poor security.
“In 2022, it took an average of 277 days—about 9 months—to identify and contain a breach. Shortening the time it takes to identify and contain a data breach to 200 days or less can save money…Average savings of containing a data breach in 200 days or less: $1.12M.”
Official FBI IC3 Definitions:
Data Breach: A data breach in the cyber context is the use of a computer intrusion to acquire confidential or secured information. This does not include computer intrusions targeting personally owned computers, systems, devices, or personal accounts such as social media or financial accounts.
Personal Data Breach: A leak/spill of personal data which is released from a secure location to an untrusted environment. Also, a security incident in which an individual’s sensitive, protected, or confidential data is copied, transmitted, viewed, stolen, or used by an unauthorized individual.
“Personal Data Breach” fell under the Top 5 Crime Types in FBI’s IC3 2022 report (the most recent report as of this date), however “Data Breach” did not.
| MEASUREMENT | YEAR | PERSONAL DATA BREACH | DATA BREACH |
| VICTIM COUNT | 2022 | 58,859 | 2,795 |
| VICTIM COUNT | 2021 | 51,829 | 1,287 |
| VICTIM COUNT | 2020 | 45,330 | 2,794 |
| VICTIM LOSS | 2022 | $742,438,136 | $459,321,859 |
| VICTIM LOSS | 2021 | $517,021,289 | $151,568,225 |
| VICTIM LOSS | 2020 | $194,473,055 | $128,916,648 |
The Average cost of a data breach in the US in 2022, based on figures provided by the FBI, comes out to be roughly $1.6M (2022 victim loss divided by 2022 victim count = $1,646,314.907).
IBM states that the cost of a data breach in the US is twice the global average ($4.35M), coming in at $9.44M.
While we can’t speak to why there is such a difference in the numbers, our assumption is because not everyone reports data breaches. Regardless, data breaches aren’t cheap. Investing in some physical security keys is probably a better use of your money, not to mention, the bill will be far smaller.
Disclaimer: A portion of this article was written with the help of AI.





0 Comments